As phishing attacks gain steam and become more sophisticated, learn the simple open-source toolkits available to investigate adversary websites, the people who build them and the trends that can be discovered.
In today's interconnected world, almost all organizations, governments and individuals depend on digital technology to perform some or all of their work. The significant reliance on high-tech systems necessitates robust, proactive security measures, so cyber attackers can be halted even before they attempt to compromise organizations' IT systems.
Cyberthreat intelligence has emerged as a crucial need to boost cyber defenses by proactively collecting and analyzing cyber threat data from various sources to understand adversaries' attack methods and techniques. Armed with this knowledge, organizations can better respond to the ever-increasing number and sophistication of cyberattacks, thereby enhancing their overall security posture.
To understand that infrastructure, we will focus on a key element of cyberthreat intelligence data: detecting and tracking attackers' IT infrastructure. This has become very important as part of any proactive cyber defense strategy by using open-source intelligence (OSINT) methods.
Adversaries' IT infrastructure tracking methods
DNS historical data is considered a rich source of information for tracking the infrastructure of cyber attackers. For instance, attackers commonly reuse domains, IPs or hosting providers; historical DNS records can reveal patterns, past malicious activity and connections between different attack campaigns.
Why is DNS historical data important for tracking attackers?
DNS historical data refers to the set of updates and modifications made to domain DNS settings over time. For example, DNS historical data consists of past records of domain names, IP resolutions, name servers and other DNS-related configuration changes, which include:
- A/AAAA records (IP addresses linked to domains)
- MX records (mail servers)
- NS records (name servers)
- TXT records (often used for verification or malware C2)
- WHOIS changes (ownership, registrar, and registration dates)
Such data is important for OSINT gatherers because it allows them to:
- Identify attacker IT infrastructure – By identifying past and present infrastructure linked to malicious domains.
- Attack attribution – Reveal the connections between different IPs, domain names and hosting providers used during different attack campaigns (such as different phishing email campaigns).
- Identify attack patterns – Adversaries often reuse the same infrastructure across different attacks; analyzing historical data helps reveal these patterns.
- Facilitate tracking malware and phishing campaigns – By showing where malicious domains were previously hosted, OSINT gatherers can better track fast-changing networks.
Tools and methods for DNS historical data analysis
Here are some tools to collect historical DNS information:
- VirusTotal – Provides historical DNS resolutions, WHOIS and malware detections. To use this service, search a domain >> "Relations" tab (see Figure 1)
- SecurityTrails – Provides extensive DNS history, subdomain data and IP ownership records
- Farsight DNSDB – The largest passive DNS database
- CIRCL Passive DNS – A free database that stores historical DNS records from various resources
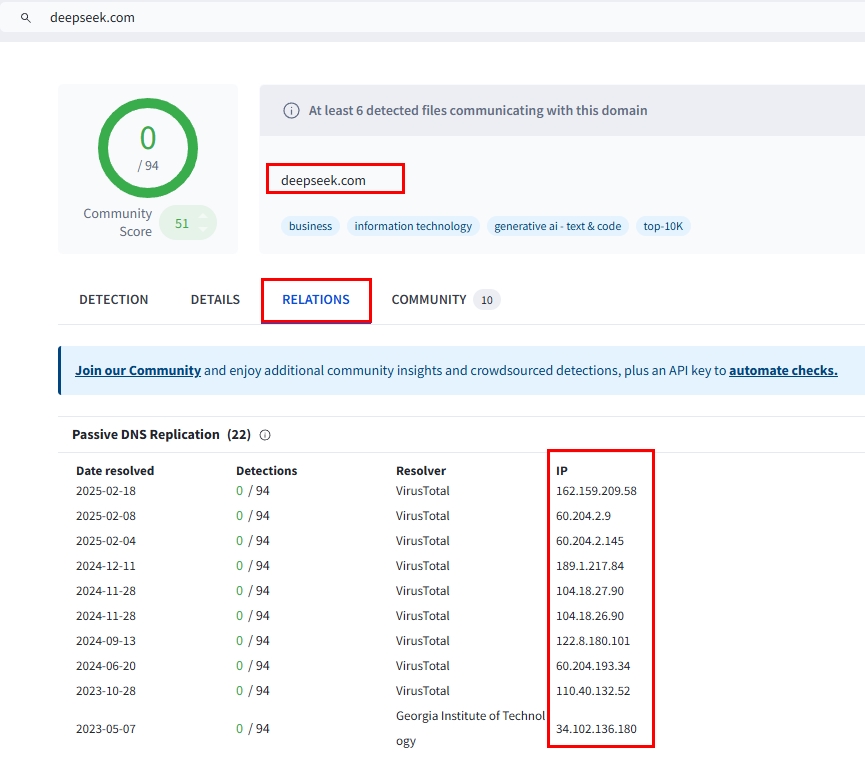
Figure 1 - Using VirusTotal to track DNS IP changes over time
Domain registration historical information
Domain registration data refers to the information collected when someone registers a domain name through a registrar (e.g., GoDaddy, Namecheap, Enom). This data is stored in a WHOIS database, which in turn is maintained by registrars and overseen by the Internet Corporation for Assigned Names and Numbers (ICANN). Historical domain registration data includes both current and past records of a domain's registration information. Inspecting this information can provide insights into its ownership, usage, and changes over time.
- Registrant information: Name, organization, email, phone number and mailing address of the domain owner (Many domain name owners obfuscate this information using a third-party privacy service)
- Registrar details: The company or service used to register the domain (e.g., Namecheap, GoDaddy)
- Registration dates: The domain's creation date, last update and expiration date.
- Name servers: Servers that host the domain's DNS records, this is used to indicate where the domain is hosted or pointed.
- Status codes: An indicator of the domain's status (e.g., active, locked, pending deletion)
- WHOIS history: Historical snapshots of WHOIS records, showing changes in ownership, contact details or other metadata over time
- Privacy/Proxy services: The use of services that hide your contact information from the public WHOIS database (e.g., WhoisGuard, Domains By Proxy)
- DNS records: The associated domain name records, like MX (mail exchange), A (address) or TXT records, which may reveal IT infrastructure details
Sources of historical data
Historical information of domain names can be acquired from various sources, such as:
- WHOIS databases – Such as Whois.com and Who.is
- Third-Party Services – Some online services aggregate and store historical WHOIS data, such as DomainTools and Whoisfreaks
- Passive DNS data - Provides historical mappings of domains to IP addresses, revealing hosting infrastructure. We can get such information from the following services/tools: Spamhaus Passive DNS, Passive DNS version 2.0, Dnsdumpster and PassiveTotal
- Internet archive – Archive websites can display deleted content hosted on a domain. Here are some services: The Wayback Machine and Archive.today
What are the key indicators to look for in registration records that point to malicious activity
When inspecting domain registration records, specific indicators can signal potential malicious activity or provide clues about the threat actors behind a domain. Below are some elements to focus on:
- Fake details: If the domain registration information contains inconsistent or fake information, such as admin@gmail.com as the registrant email address, this can point to fake information.
- Privacy services: Using proxy services to conceal the domain registration true information is suspicious. While many companies opt to use such services for spam protection purposes, if more than one suspicious domain is using privacy protection services, this can signal a red alert.
- Reused contact information: Reusing the same contact information for the domain name, such as phone, mailing address and email, could indicate that all these domain names belong to a single actor.
- Short-lived domains: When a suspicious domain is registered for one year or less, this may indicate its use for malicious purposes, such as launching a phishing campaign or serving as a command and control server in a ransomware attack.
- Bulk registration: If multiple domain names with identical name variations have been registered within the same period (same day), this could indicate a coordinated campaign.
- Shared name servers: Domain names using the same naming servers, similar to malicious domains, may indicate they all belong to the same threat actor infrastructure.
- Suspicious hosting providers: Hosting domain names on a hosting provider that is known to have lax registration terms is another red flag.
Reverse IP lookup search
A reverse IP lookup is a technique used to identify all domains and services hosted on a specific IP address. Unlike a standard DNS lookup (which resolves a domain to an IP), a reverse IP lookup does the opposite, revealing all domains associated with a given IP. This is particularly useful in OSINT investigations because attackers often use shared hosting, compromised servers, or cloud infrastructure to host multiple malicious entities' domains.
For instance, many legitimate websites and malicious actors alike may share an IP due to:
- Shared hosting environments. This is more cost-effective than using a dedicated hosting environment.
- They use a content Delivery network to boost website performance (CDNs) (e.g., Cloudflare, Akamai)
- Bulletproof hosting (used by cybercriminals to evade takedowns as such providers allow using their services without providing any legal document and accept anonymous payments)
- Compromised servers (legitimate IPs abused for phishing or malware)
By analyzing these associations, security researchers can uncover attacker infrastructure, detect phishing campaigns, or identify other malicious domains linked to the same host.
Steps to perform a reverse IP lookup
- Extract the IP from a suspicious domain using the command line prompt (see Figure 2).
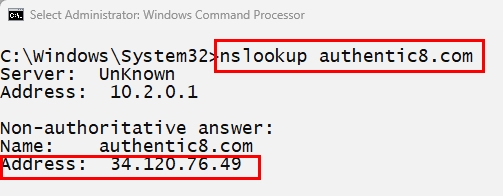
Figure 2 - Extract the domain name IP address using the Windows command line prompt
- As an alternative method, we can use online services or tools to perform a reverse IP lookup of any domain name:
What insight can OSINT gatherers know from inspecting associated domains and services?
Performing a reverse IP lookup can reveal:
- Attack infrastructure clustering – For example, multiple phishing or malware domains hosted on a single IP may indicate a coordinated malicious campaign.
- Shared hosting abuse – Some legitimate servers could host a malicious site; this practice is often seen in supply-chain attacks.
- Bulletproof hosting patterns – IPs known for hosting multiple malicious sites over time. A bulletproof hosting provider typically operates from jurisdictions with minimal cybercrime legislation or enforcement capabilities.
- Historical context – If an IP address was previously flagged for spam or attacks, new domains associated with it could be suspicious.
- False positives – Some IPs (like CDNs) host thousands of domains, which requires additional filtering.
Tracking adversary IT infrastructure through OSINT represents an essential component of proactive cyberdefense. By systematically analyzing DNS historical data, domain registration information, and IP associations, security teams can identify malicious patterns, attribute attacks, and predict future campaigns before they escalate. This intelligence-driven approach transforms organizations from reactive victims to prepared defenders.
Investigating safely
When investigating adversary infrastructure networks, researchers must protect themselves and their data. All too often in digital investigations, “the hunter can become the hunted” as they say. For a one-time-use, disposable browser option with built-in analysis tools and capabilities, cyberthreat analysts, researchers and security professionals prefer Silo, the digital investigations platform. Silo gives the flexibility to allow persistent data when it benefits the researcher and shed all attribution when it doesn’t.
Learn more about why 750 leading organizations and dozens of Fortune 1000 companies prefer Silo. Sign up for a demo.
Tags Anonymous research OSINT research Threat intelligence

